Quick Navigation:
| |
Safety and Security in the Cyber World
Understanding the Cyber World
- The Cyber World is a digital space where individuals share resources, access information, and interact with others globally via the Internet.
- Just as in the real world, users must remain cautious and alert to protect themselves from various online complexities and risks.
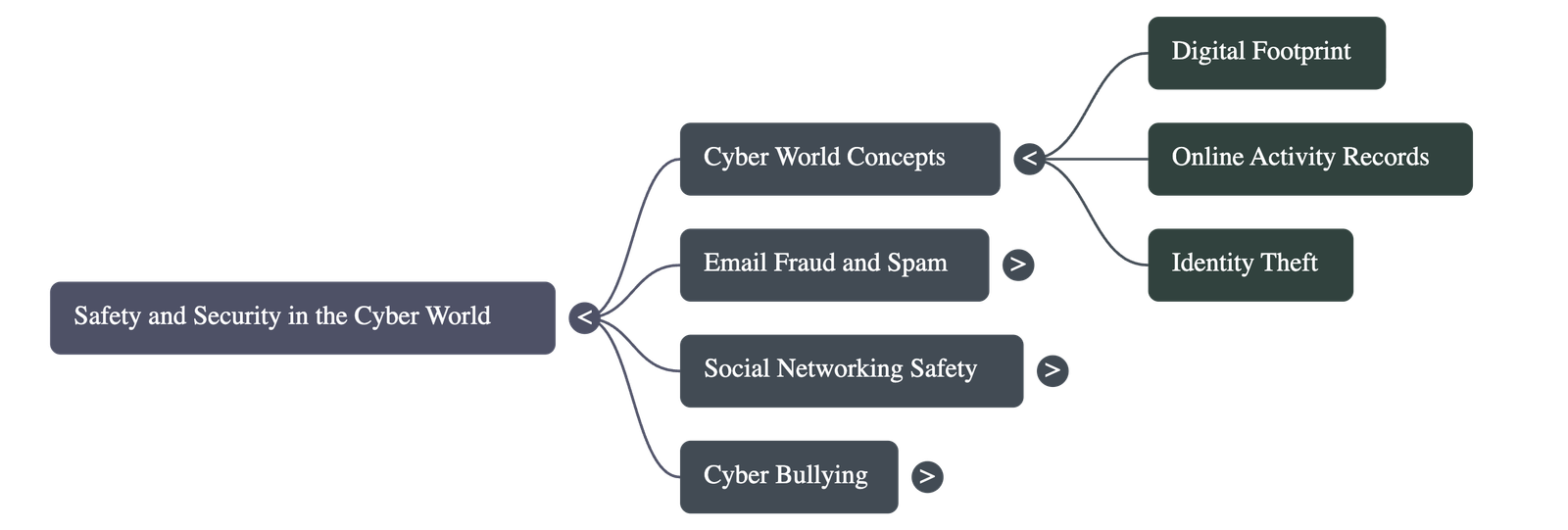
- A Digital Footprint refers to the trail of information about a person that remains on the Internet due to their online activity. This information often persists even after it has been deleted.
Email Safety and Fraud Prevention
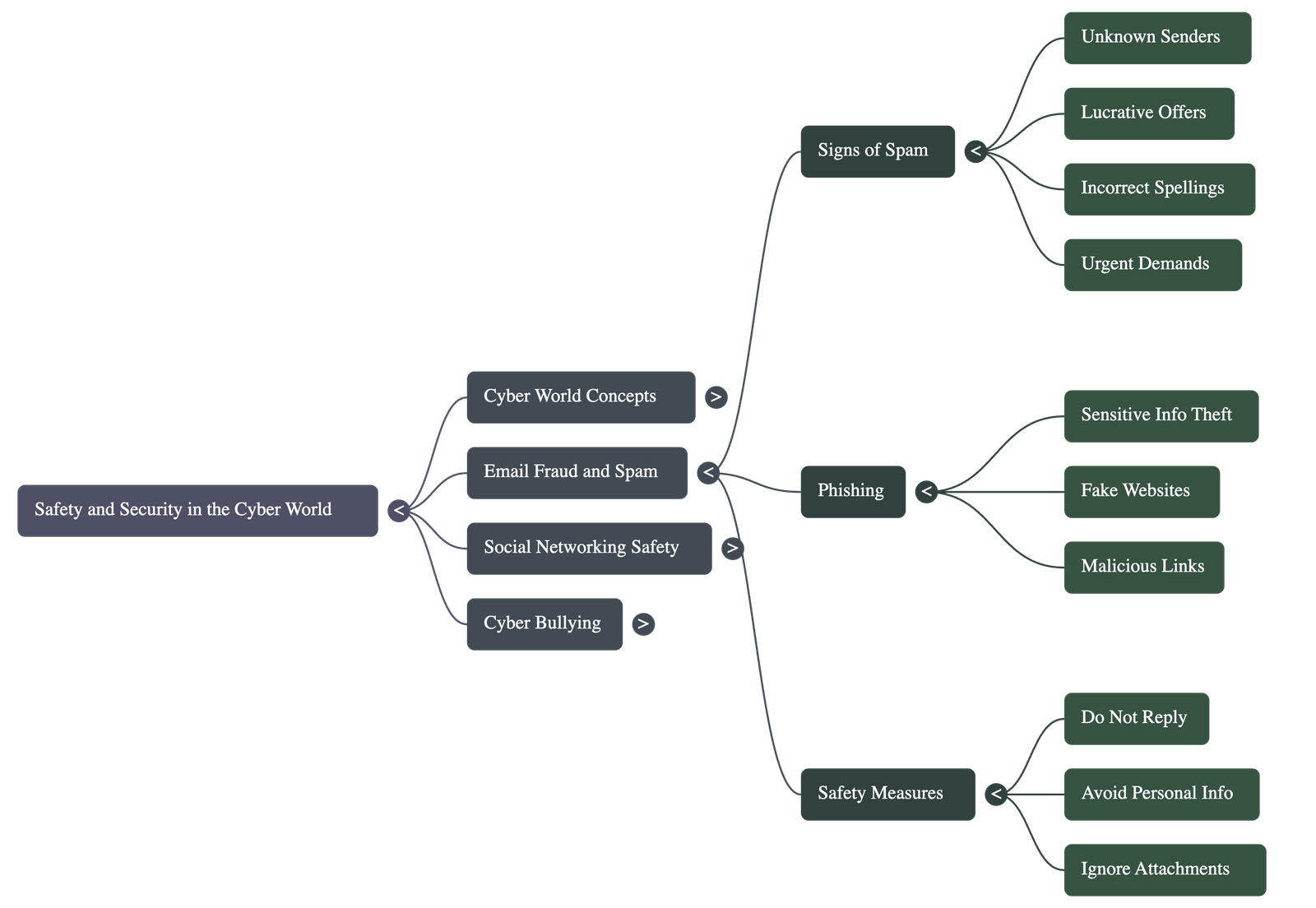
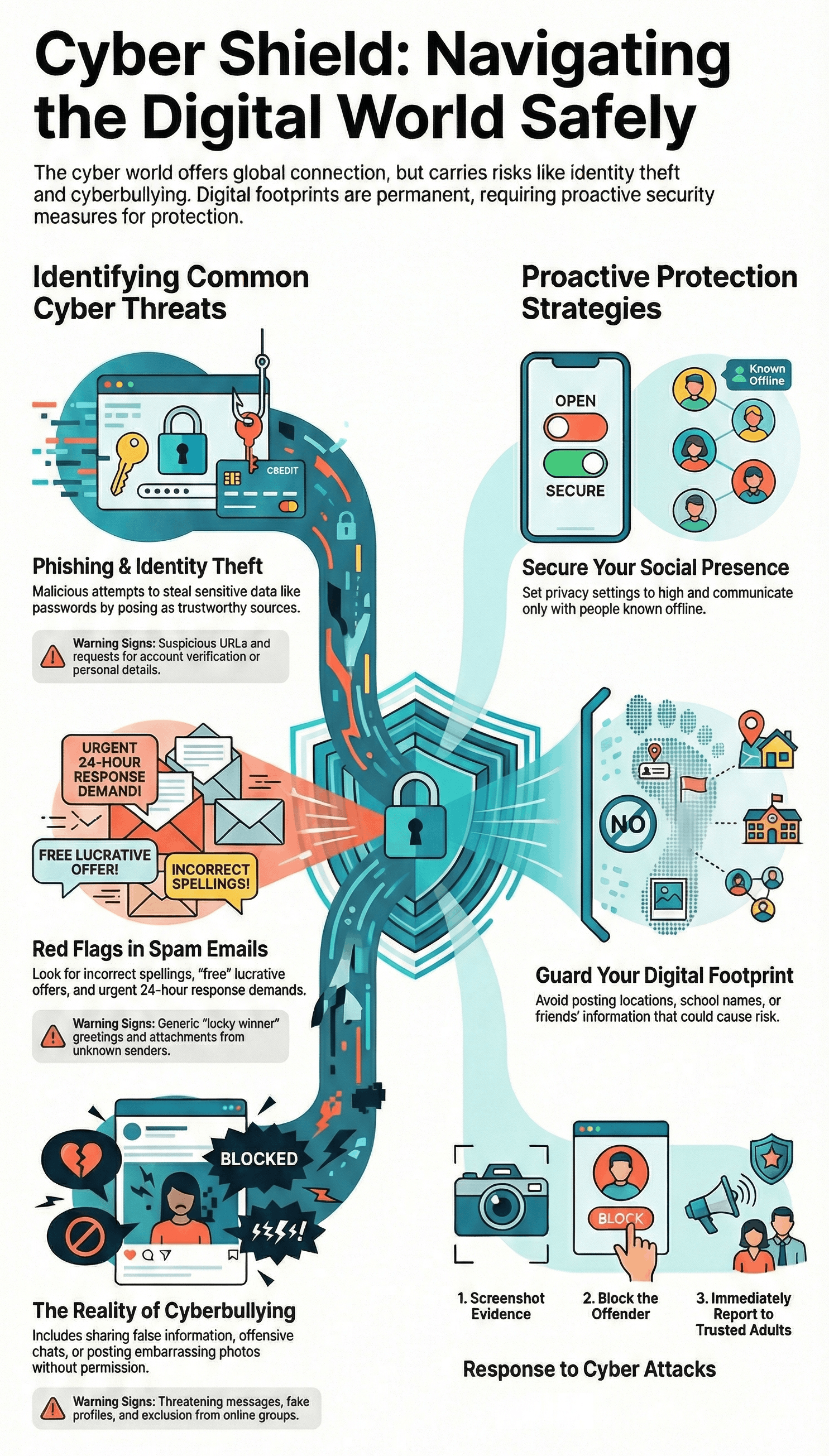
- Spam Mails: These are unsolicited emails from unknown sources, often with malicious intent. They frequently use lucrative offers or claims of "winning a lottery" to tempt users into following harmful instructions.
- Phishing: A fraudulent attempt to obtain sensitive information like usernames, passwords, and credit card details by posing as a trustworthy entity.
- Malware: Malicious software that can be installed on a device if a user clicks on suspicious links or downloads unknown attachments.
- Protective Measures:
- Never reply to emails from unknown senders.
- Avoid providing personal details like school names, addresses, or parent's information.
- Check URLs carefully to identify fake or unsecure websites.
- Do not forward suspicious emails or excessive "chain" messages.
Safe Social Networking
- Social networking sites allow global connectivity but require strict safety precautions because it is difficult to verify a person's true identity online.
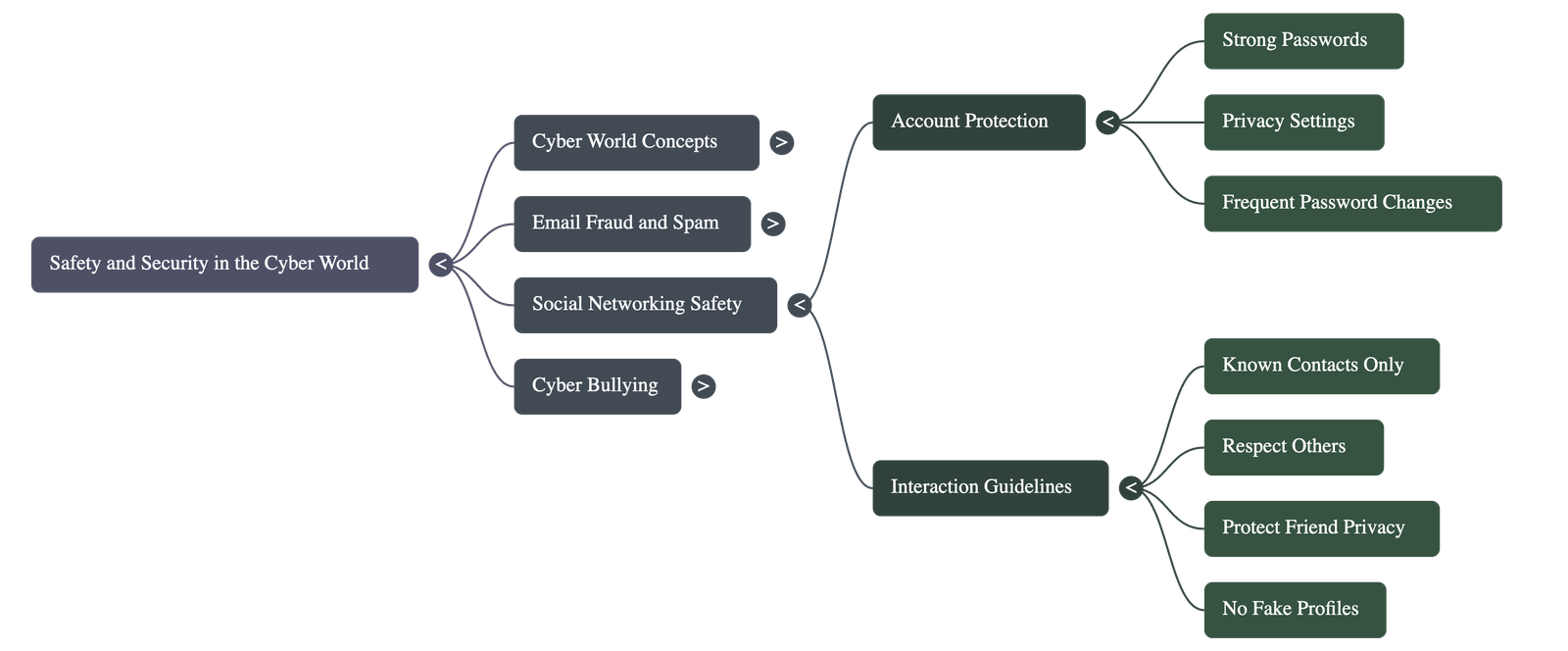
- Privacy Settings: Users should carefully configure privacy settings to control what information is shared publicly.
- Account Security: Passwords should be strong, changed frequently, and never shared with anyone except parents or guardians.
- Responsible Posting:
- Avoid sharing sensitive information, photos, or videos that could leave a permanent negative digital footprint.
- Do not post friends' information, group photos, or locations without their permission to protect their privacy and safety.
- Never create fake profiles or forward unverified information.
- Always log out immediately after using an account and never leave it unattended while logged in.
Cyber Bullying and Identity Theft
- Identity Theft: The deliberate use of another person’s identity to obtain credit, benefits, or to defame them. This is a common cybercrime that can severely damage a person's reputation.
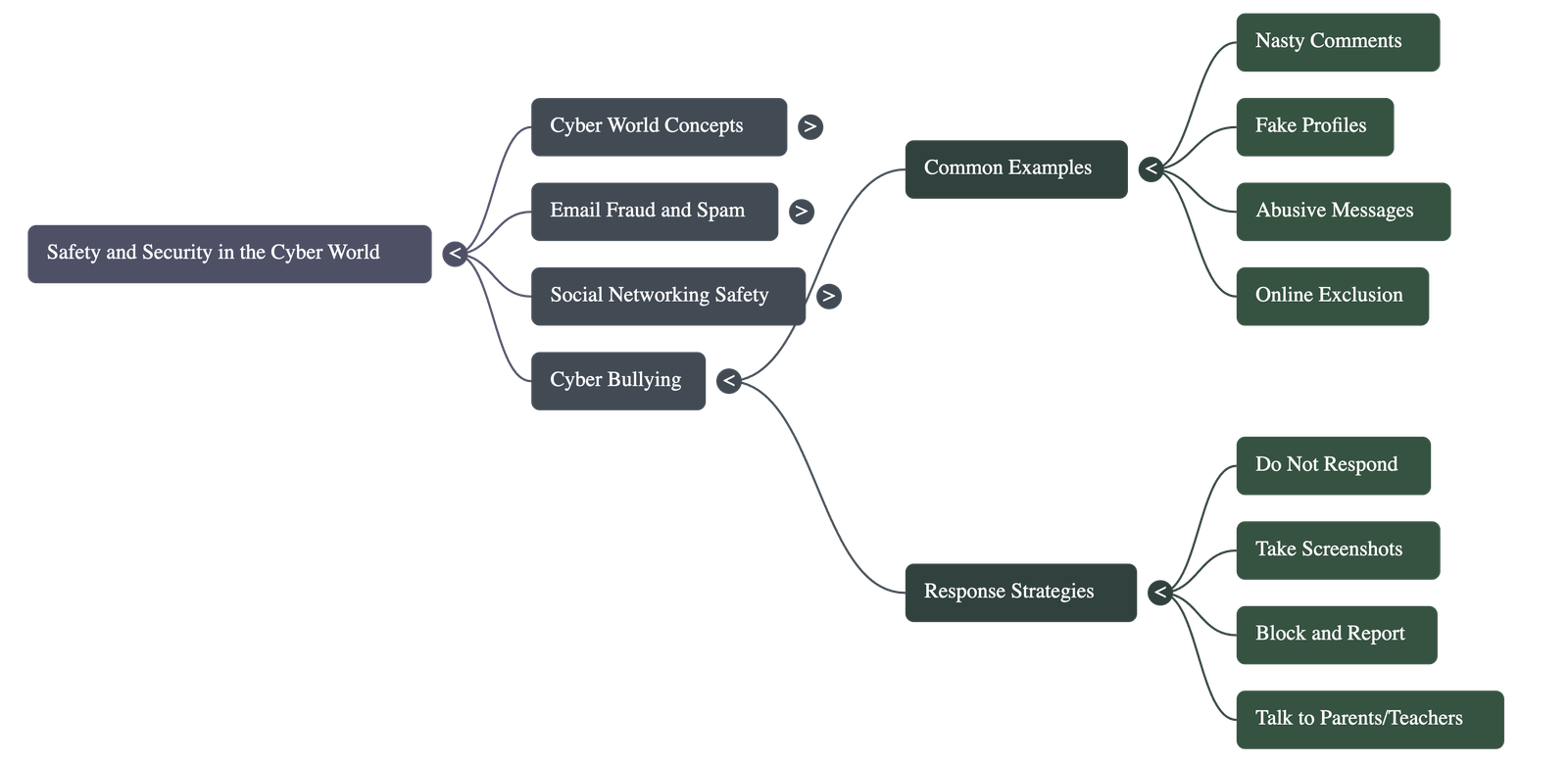
- Cyber Bullying: This includes posting nasty comments, creating fake profiles to defame someone, sending threatening messages, or sharing embarrassing photos without permission.
- Legal Consequences: Cyber bullying is a serious offense punishable under Cyber Law.
- Action Steps for Victims:
- Do not respond: Retaliating can make the situation worse.
- Keep evidence: Take screenshots of the bullying behavior.
- Block and Report: Use platform tools to stop the offender and alert the service provider.
- Seek Help: Talk to parents or teachers immediately; do not deal with it alone.
Quick Navigation:
| |